- Dynamic Vlan Assignment Microsoft Nps Radius Server Download
- Dynamic Vlan Assignment Microsoft Nps Radius Server Server
Dynamic VLAN Assignment + NPS Just to follow up, I've successfully implemented this and the client is happy with the outcome of the project. Thanks for your help Steve. Dynamic vlan assignment nps, dynamic vlan assignment cisco 2960, dynamic vlan assignment with windows radius server, dynamic vlan 802 1x. Dynamic vlan cisco 802 1x, dynamic vlan microsoft nap.
Situation:
I am trying to get 802.1X working for me. I want RADIUS server to dynamically assign VLANs to ports based on RADIUS reply attribute for particular user. I have an HP E2620 switch and a FreeRADIUS server. The supplicant is a Windows 8.1 machine
I referred to this document on freeradius website.
What I've done so far:
On FreeRADIUS I created a user with such parameters:
I also tried Tunnel-Pvt-Group-ID instead, but it doesn't work on FreeRADIUS, just barks at me (I saw this on resources for configuring on Microsoft NPS, one of these). Also I tried values '802', 802, 6 for tunnel medium type.
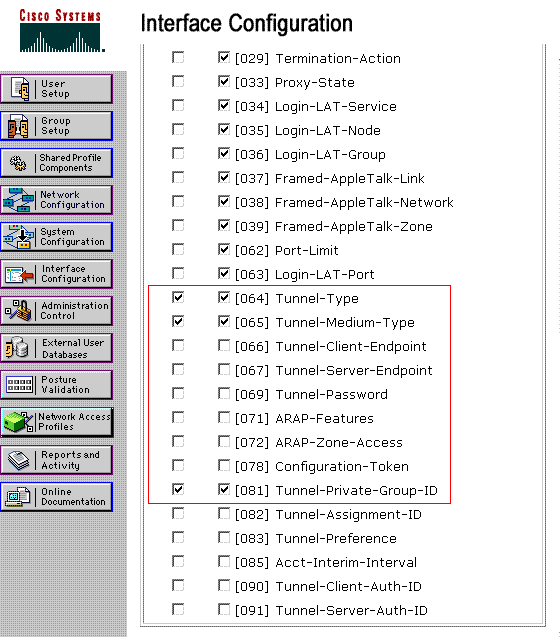
Dynamic Vlan Assignment Microsoft Nps Radius Server Download
Also I tried to use actual VLAN name instead of VLAN-ID as Group ID value. Anyway its datatype is string.
I configured the HP switch to use this RADIUS server for AAA and set this up for port 10:
VLANs:
Notes:
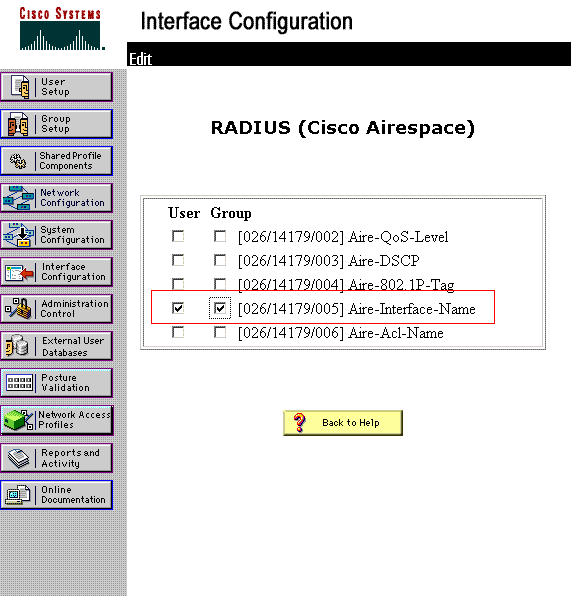
Port 10 also has untagged VLAN 150 assigned to it:
vlan 150 untagged 10. And I can't get rid of the static assignmentAll VLANs listed above are present in switch's VLAN database.
Whenever I plug into this port it asks me for credentials; after I succeed with authentication it just sends me to VLAN150 and if I try to fail I get to VLAN200.
I enabled 802.1X authentication on Windows connection just like described here.
I tried enabling GVRP - it doesn't change anything
Diagnostic/show command output:
Static VLAN assignment for Port 10. VLAN 150 untagged
Inshow loggingI see this:
show port-access authenticatoroutput:
Dynamic Vlan Assignment Microsoft Nps Radius Server Server
RADIUS user test:
This is what I saw in TCPdump on the RADIUS server. I was capturing outgoing UDP traffic with source port 1812. It's what my switch gets (if it does actually, not sure how to check that...)
Debug:
After that I unplugged and plugged in the cable and did show debug buffer and here is the copy-paste of it. It's weird, nothing is said about any attributed related to VLAN.
Questions:
What am I doing wrong?
I've read in a bunch of resources that if the RADIUS assigns a VLAN ID switch uses that in the first place. Then it falls back to Authorized VLAN configured for Port-Access Authenticator if authentication succeeds. If that is not present it assigns Untagged VLAN configured on the port. Why don't I get that behavior?
I kind of start to think the attribute Tunnel-Private-Group-Id is not supported on these switches. It seems every resource refers to Tunnel-Pvt-Group-Id instead (configuring on Microsoft). Too bad I don't have Windows Server to check.
Maybe it's firmware related? Didn't try to upgrade yet, I use RA_15_06_0009.swi and there's RA_15_14_0007.swi out there already
Update
Just tried on a 3500yl-24G-PWR model and still doesn't work. So.. I'd guess, switches just don't get the config from the RADIUS server (or did I use incorrect attributes or operators?). How can I troubleshoot that?
3 Answers
Alex, hеllo there!
Ive builded test environmet for you, so i am using freeradius 2.1.12+dfsg-1.2 (on debian), and switch hp 2650. Ive just repeated your config, and have no problems with this. My test procurve ip 10.0.10.29, test freeradius ip 192.168.2.60.
procurve config:
/etc/freeradius/users:
/etc/freeradius/radiusd.conf:
And i`ve used this manual, to enable 8021x in windows:
But, I`ve disabled usage of logged user creds.
So, if user creds are correct, i have this message in /var/log/freeradius/radius.log
and on my switch ive got:
If creds are incorrect:
maybe you havent enabled 8021x in windows? I hope this helps to you man.
Wow, I would have never though of this one. It was just a random solution.
So, the problem was with authorize section in my default site configuration at /etc/raddb/sites-enabled/default, it was kind of default. I don't really know what's up with that (if you, guys, know, comment on that, please), gonna do some research on that; here it is:
I commented this out and replaced with just:
I was not hoping any more to ever get it working and then I reconnected and... it happened, just randomly and I'm so excited now! I got assigned a VLAN dynamically:
Debug:
SW # show port-access authenticator 10 vlan - still shows Unauthorized VLAN 200 and Authorized VLAN 150
SW # show vlans ports 10 detail - And the untagged VLAN on port 10 got set to VLAN 100
SW # show port-access authenticator
Also, if you want it to work, you have to create all required VLANs on the switch, otherwise you'll get this kind of stuff:
and the Windows will just say: Authentication failed which is kind of confusing too.
Didn't quite get it to work with unknown VLANs in spite of the fact GVRP was enabled, aaa port-access gvrp-vlans was set and I also explicitly set unknown-vlans learn on interface 10, but oh well...nvm.
You need to add the following command:
aaa port-access authenticator 10 auth-vid 150
This would tell the switch that port 10 will use the auth-vid assigned VLAN for authenticated devices unless it gets a different value from RADIUS. Without this, it will just use the configured port value and ignore any RADIUS provided VLAN assignments.
I did some digging and found this tidbit in one of my saved HP docs:
If the RADIUS server specifies a VLAN for an authenticated supplicant connected to an 802.1X authenticator port, this VLAN assignment overrides any Authorized-Client VLAN assignment configured on the authenticator port. This is because both VLANs are untagged, and the switch allows only one untagged VLAN membership per-port. For example, suppose you configured port 4 to place authenticated suppli- cants in VLAN 20. If a RADIUS server authenticates supplicant “A” and assigns this supplicant to VLAN 50, then the port can access VLAN 50 for the duration of the client session. When the client disconnects from the port, then the port drops these assignments and uses only the VLAN memberships for which it is statically configured.
YLearn♦YLearn